Data Sharing Risks: Big Tech’s Careless Past and LightUp.Cloud’s Secure Solution
In the digital age, data is a coveted asset, driving innovation and profit for tech giants. However, the careless handling of user data by companies like Google, Facebook, Dropbox, and Amazon has led to significant breaches, eroding trust and prompting stricter regulations. As Karl Marx noted in *Das Kapital*, “With adequate profit, capital is very bold,” a sentiment reflected in big tech’s willingness to exploit user data for financial gain. This article examines historical data leak cases, categorizes their causes, and highlights how LightUp.Cloud empowers users with secure, local storage to mitigate these risks, ensuring control and transparency over their data.
The Profit Motive Behind Data Exploitation
Tech companies compete fiercely to amass user data, often using it to train AI models or sell to advertisers, as Marx’s observation suggests: high profits embolden corporations to sidestep ethical boundaries. For instance, Microsoft’s acquisition of LinkedIn enabled it to leverage user data for AI training, enhancing its competitive edge. Similarly, an Amazon employee at a Dublin Python conference revealed the company’s dedicated department for analyzing AWS service usage, allegedly to compete with clients by replicating their offerings. These practices underscore the need for users to prioritize local storage solutions that prevent data exploitation.
Notable Data Leak Cases and Their Causes
Big tech’s history is riddled with data breaches, categorized by negligence, insecure infrastructure, and intentional data sales:
Negligence and Insecure Practices
- Google’s Unencrypted Transfers: For years, Google transmitted user data, including emails and search queries, over public networks in plain text without encryption, exposing it to interception. This practice persisted until public outcry and regulatory pressure forced adoption of HTTPS in the mid-2010s, highlighting a careless approach to user privacy.
- Dropbox’s 2012 Breach: Hackers exploited stolen employee credentials to access 68 million user accounts, with email addresses and passwords leaked online in 2016. Dropbox’s delay in disclosing the breach and lack of user-level encryption exacerbated the damage.
- Amazon’s Internal Leaks: In May 2017, Amazon employees discovered unsecured American Express credit card numbers on its internal network, accessible for months. Limited audit logs (90 days) prevented determining if the data was abused, revealing lax internal controls.
Insecure Infrastructure
- Dropbox’s AWS S3 URL Guessing: Dropbox’s reliance on AWS S3 allowed attackers to guess file URLs, enabling unauthorized downloads of user files. Misconfigured S3 buckets, a recurring issue across AWS clients, exposed sensitive data due to inadequate security settings.
- Amazon’s Twitch Breach (2021): A server configuration error exposed 128 gigabytes of Twitch data, including source code and streamer earnings, due to lax AWS security practices. Amazon’s lack of public comment further fueled distrust.
- Elastic Database Leak (2025): A misconfigured cloud server exposed 184 million plaintext login credentials for services like Google, Facebook, and Amazon, totaling 47 GB, discovered by researcher Jeremiah Fowler.
Intentional Data Sales and Misuse
-
Facebook’s Data Sales:
Facebook sold user data to advertisers and third parties, including Cambridge Analytica, which misused it
for political targeting. Allegations surfaced that data was shared with Chinese entities, raising national
security concerns. A 2023 EU fine of $1.3 billion for illegal U.S. data transfers underscored GDPR
violations.
- Amazon’s Customer Data Harvesting: A Chinese data firm harvested millions of Amazon customer records, reminiscent of Cambridge Analytica, exploiting a program allowing sellers to extract metrics. Amazon’s response was to limit data sharing, but the incident exposed systemic vulnerabilities.
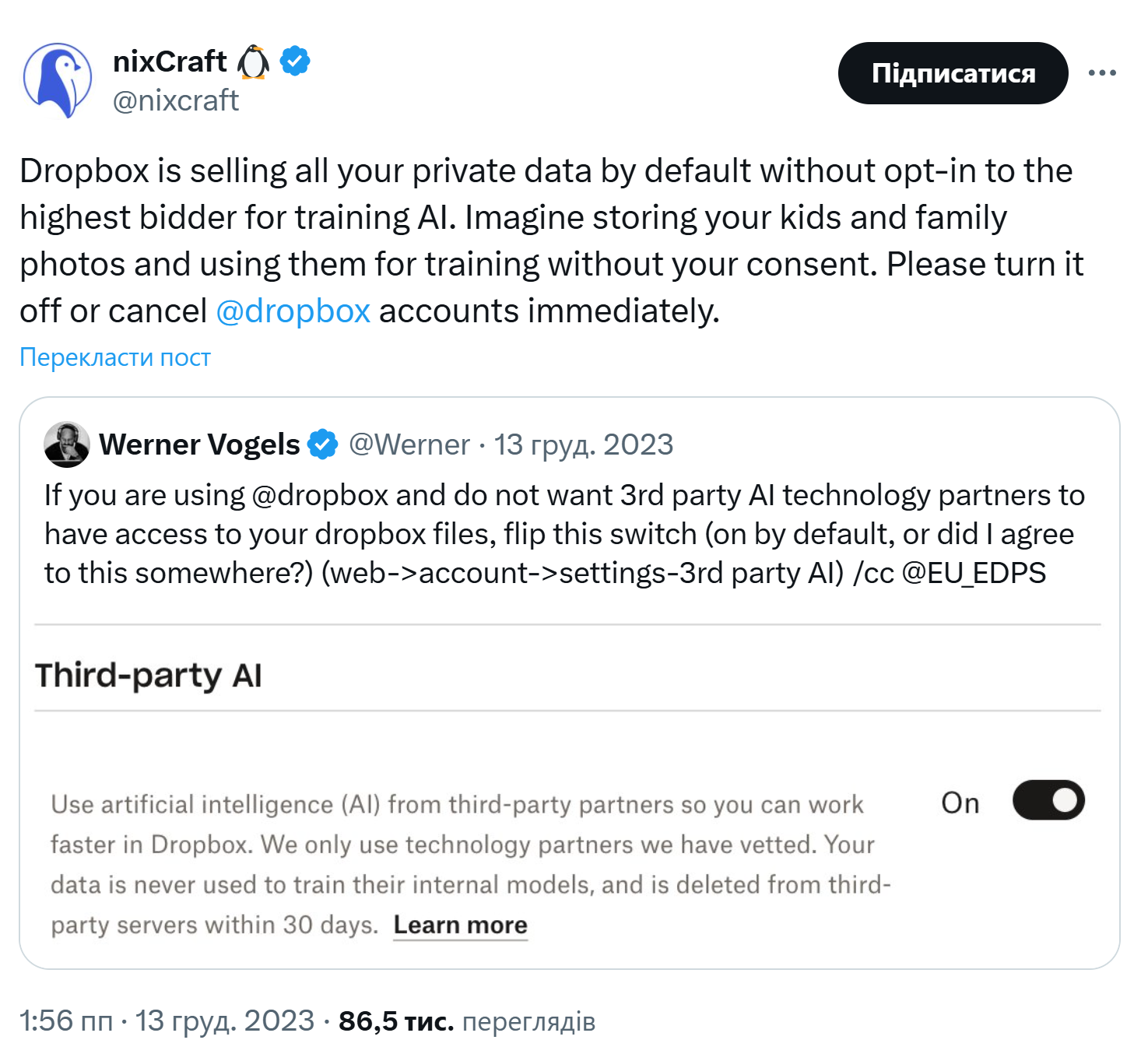
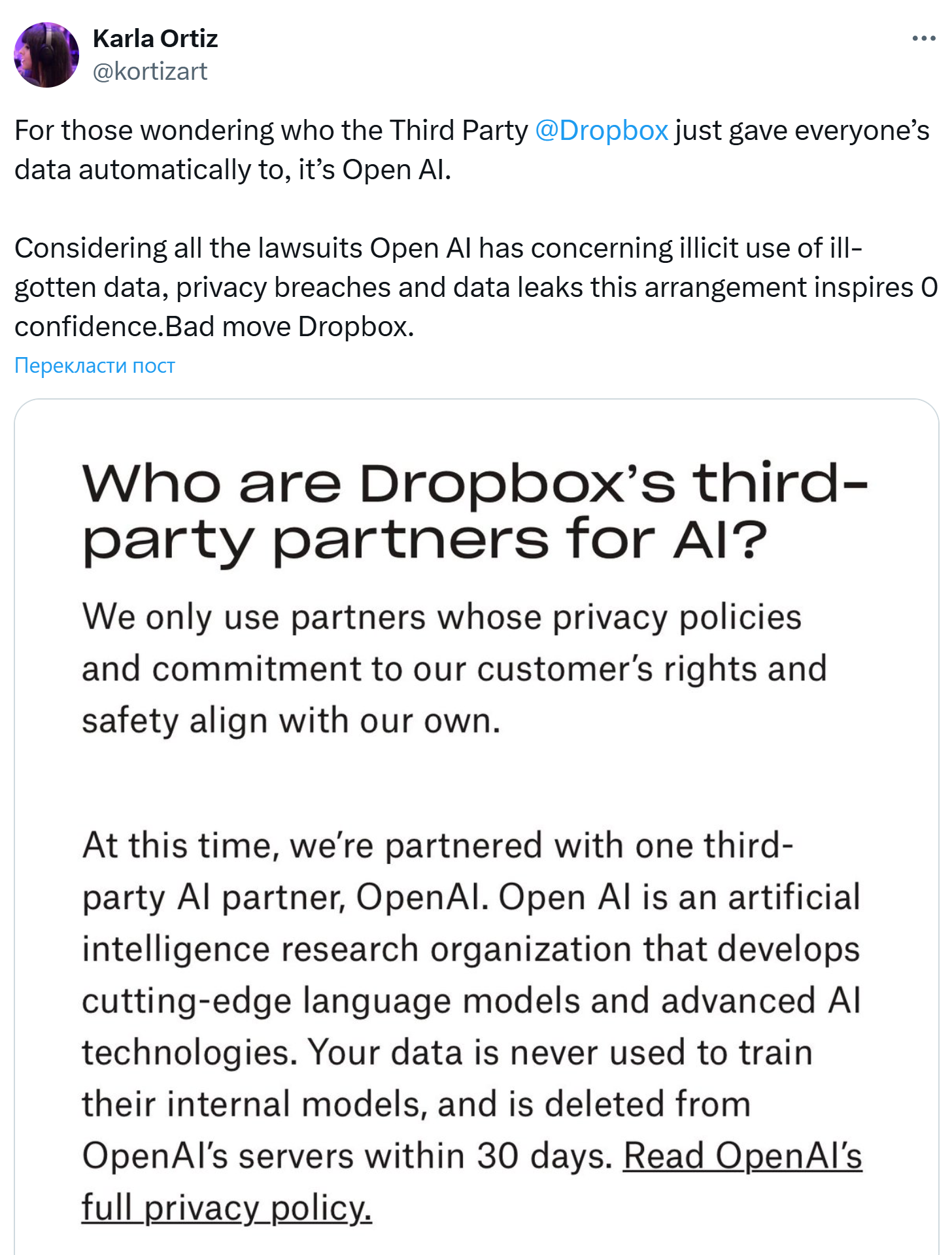
-
Dropbox and Open AI (2023):
Dropbox faced backlash for sharing user data with Open AI for AI training without explicit consent,
prompting users to disable the feature or cancel accounts.
Regulatory Responses: EU and U.S. Security Audits
These breaches have spurred stringent regulations. In the EU, the General Data Protection Regulation (GDPR) mandates security audits, data residency, and user consent, with fines up to €20 million or 4% of annual revenue. In the U.S., laws like the California Consumer Privacy Act (CCPA) and sector-specific regulations (e.g., HIPAA, FINRA) require regular audits to ensure data protection. These laws reflect the need to counter big tech’s profit-driven negligence, as Marx’s critique of capital’s audacity suggests.
Risks of Cloud-Based Storage
Cloud providers like AWS, used by Dropbox and others, introduce risks:
- Unauthorized Access: AWS’s terms allow Amazon to access user data, and misconfigured S3 buckets have led to breaches.
- AI Training Exploitation: Companies like Microsoft use LinkedIn data for AI training, often without transparent consent, raising privacy concerns.
- Market Manipulation: Amazon’s alleged practice of analyzing AWS usage to compete with clients exploits data for profit, undermining trust.
These risks highlight the need for users to control where and how their data is stored.
LightUp.Cloud: Empowering User Control
LightUp.Cloud offers a secure, on-premises alternative to mitigate data sharing risks:
- Local Storage: Host servers locally or in chosen datacenters, ensuring data residency and preventing unauthorized access, unlike AWS-based platforms.
- Robust Security: SSL encryption, process isolation via the Erlang Virtual Machine, and granular access controls protect data, aligning with GDPR and CCPA.
- Audit Logs: Tracks all file operations for transparency, supporting regulatory audits.
- No Data Exploitation: Data is neither sold nor indexed for AI, unlike Dropbox’s Open AI partnership.
-
- Cost Efficiency: At $588 per year for 5 terabytes and unlimited users, it saves up to five times compared to Dropbox Business ($2,250/year).
- Flexibility: Open-source architecture and S3-compatible API eliminate vendor lock-in, empowering users to choose their storage solution.
With speeds up to 10 gigabits per second, LightUp.Cloud ensures rapid access to large files, ideal for architects or healthcare providers.
Building a Trustworthy Future
Big tech’s profit-driven data practices, as Marx warned, prioritize gain over ethics, leading to breaches and mistrust. LightUp.Cloud empowers users to store data locally, know who has access, and avoid exploitation, offering a path to secure, transparent data management. Deployable with a three-click setup using the Cloud Development Kit, it provides affordable, high-speed storage for small businesses. Visit LightUp.Cloud to take control of your data today.

